Platform
Argos Platform
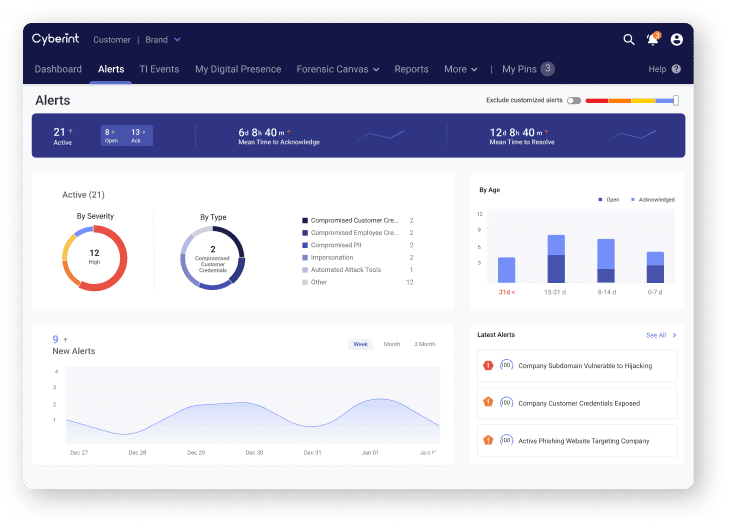
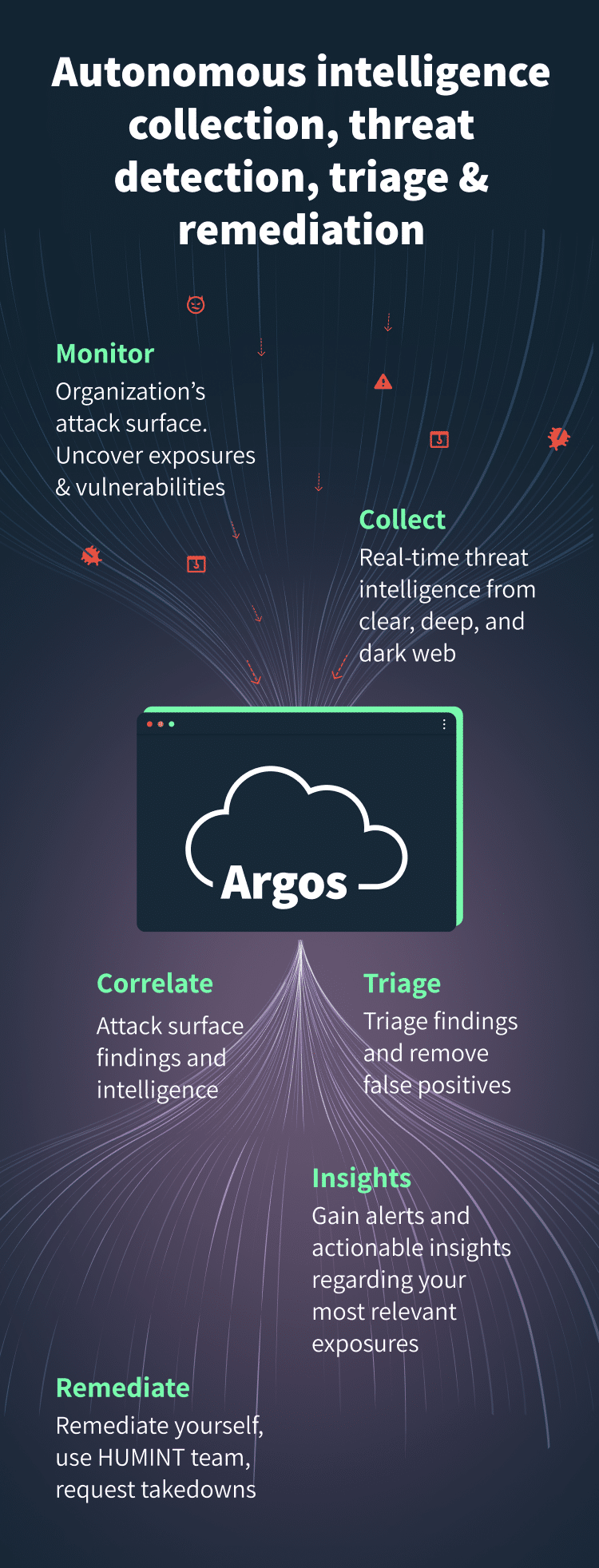
Manage exposure, prioritize threats, and reduce cyber risk with Argos, Cyberint’s Impactful Intelligence platform. Protect your organization from an array of external cyber risks with a single comprehensive solution.
Real-time threat intelligence, tailored to your attack surface
Get Holistic Coverage of Multiple Business Risk Areas
Attack Surface management
From exposed web Interfaces and cloud Storage exposure to email security issues and open ports, Argos’ autonomous discovery maps out your external exposures and prioritize for impactful remediation.

Brand Protection
Secure company’s official social media profiles, detect and take down impersonation, Intellectual Property Infringement, unauthorized trading, defacement, and more.

Phishing Prevention
Drastically reduce response time and the number of attacks, detect and take down website cloning before malicious clones go live. Request take down of phishing pages in a click of a button.

Attackware
Get early warnings about malicious files, automated attack tools, business logic bypass proof of concepts. Learn who’s on attackers target lists, understand their M.O> and motivations.

Fraud
From refund and coupon fraud all the way to money laundering and extortion – Argos provides you with real time intelligence from the clear, deep, and dark web to help you minimize your organization’s fraud rate.

Data Leakage
Get early warning of compromised PII and/or access tokens, internal information disclosure, insider malicious activity, compromised employee or customer credentials to block, remediate, and prevent the next attack before it happens.

Frictionless enrichment through APIs and chrome extensions deliver maximum impact in real time
APIs and feeds
Contextual vulnerability intelligence and indicators of compromise (IOCs) APIs and daily feeds for enriching your security platforms, blocklists, threat research, and threat hunting activities with IOCs and context.
Chrome extension
Enrich any IOC and get its risk score, attribution, confidence and more. Detect C2 Servers, Botnets, Infected Machines and more within any webpage in a click of button. Works perfect with your web interfaces of SOC systems, SIEM, EDR, and any blogs and news sites